Managing Secrets
Historically, secret values like passwords or auth-tokens are often saved as environment variables on local machines or CI/CD servers. This imposes both, security issues because other processes can access these environment variables and inconveniences when a build must be executed locally for emergency reasons (server downtime). NUKE has an integrated encryption utility, which can be used to save and load secret values to and from parameter files.
Our custom encryption utility is provided "AS IS" without warranty of any kind.
The implementation uses your password, a static salt, 10.000 iterations, and SHA256 to generate a key-derivation function (RFC2898), which is then used to create a crypto-stream to encrypt and decrypt values via Advanced Encryption Standard (AES).
Please review the implementation carefully and contact us about any possible flaws.
Adding & Updating Secrets
You can start managing your secrets by calling:
nuke :secrets [profile]
When your parameter file does not contain secrets yet, you'll be prompted to choose a password. Otherwise, you have to provide the original password chosen.
On macOS you can also choose to generate a password and save it to your keychain in order to profit from native security tooling.
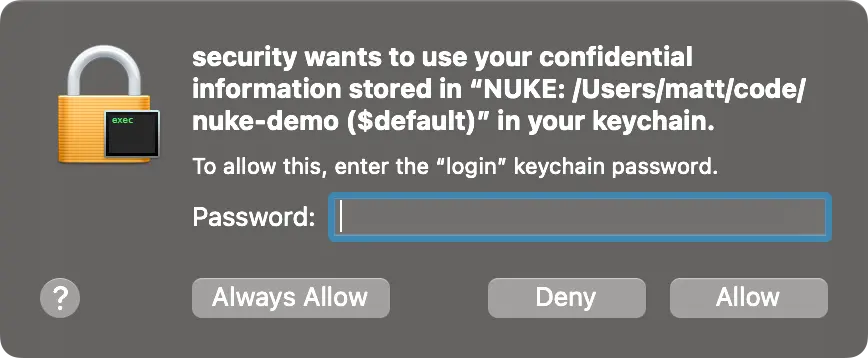
Afterwards, you can choose from a list of secret parameters, to either set or update their values, and finally accept or discard your changes:
Use Space to pause/play, ⬅ and ⮕ to seek backward/forward, or F to fullscreen.
When secrets are saved to a parameters file, they are prefixed with v1: to indicate the underlying encryption method:
{
"$schema": "./build.schema.json",
"NuGetApiKey": "v1:4VDyDmFs4Pf6IX8UvosDdjOgb23g0IXs0aP/MBqOK+K6TB8JuthtPgRUrUsi9tLD"
}
Removing Secrets
If you want to delete a secret, you can simply remove it from the parameters file. In the event of a lost password, you have to remove all secrets and re-populate the parameters file via nuke :secrets.